ICMTC CTF — DFIR Challenge Writeup “StealthyRansom”

First, let’s read the description of the challenge:
` A ransomware has infected this machine and left a ransom message.
Find the process that created the ransom message, then provide the flag. `
Let’s analyze artifacts for this challenge:

I have 3 types of artifacts. Let’s analyze event logs. I will use EvtxeCmd which is a great tool for analyses. I used this command for it:
`EvtxECmd –d folder — csv outputfolder `

This is the result after a long time of analysis. I didn’t find anything.
Let’s go to the second artifact registry. I used recmd and registry explorer. I will focus on system ,software , and security hives.

And after analysis, I didn’t find anything. All findings here and previous artifact is an RDP connection. Let’s go to the last artifact MFT (Master File Table).
You can read all about MFT in this article:
Let’s analyze it using ‘MFTECmd’ or ‘MFTExplorer’ ( it’s so good but very slow to load the GUI). I will use MFTECmd, and this is the commond I used for it:
> MFTECmd.exe –f file –csv output folder
And this is the output result:

After that, I focused on filenames, and I found many files. Let’s hide duplicate data. Using excel from data tab, choose advanced, and mark on unique records. After that, the result is still big. I thought about where I can find ransomware in the files. I had many ideas, but I tested only the first one.
Did the user download ransomware as a crack for a program or as a portable activated program? Let’s investigate users Downloads, Documents, Photos, videos, and Desktop.
And I got it in Documents:
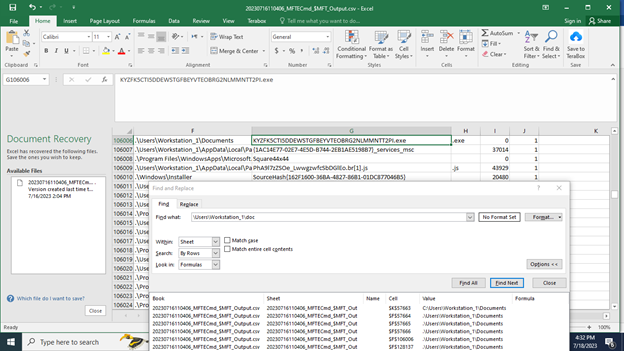
Filename: KYZFK5CTI5DDEWSTGFBEYVTEOBRG2NLMMNTT2PI.exe
However, filename is encoded and this looks like Base64.
Let’s try.
base64 not working
rot 13 not working
base 62 not working
base32 is working and I got another encoded text:
V2UtSGF2ZS1BLVdpbm5lcg==
Again let’s start with base64, and I got the final flag:

