ASCWG Qual Round Df Challenges Writeup

root of evil:
Description:During our investigation in the memory dump from the first challenge, our investigator stumbled upon a signed malicious driver that wes deployed on the machine, could you get the address of the windows API functions, which the driver was using?
Difficulty:Easy
Flag Format:ASCWG{Address1-Address2}
first i will use vol3
let’s search drivers with windows.driverscan

i found MSqPq.sys and search on it ifound this malicious driver used wth blackcat ransomware
then i dump it with vol2

python2 vol.py — profil=Win10x64_19041 -f ~/Desktop/Challenges1–2.vmem moddump -D ./

ok then let’s open it with ida

HalReturnToFrimware, KeIntitilzeEvent
ok this called apis and adresses
ok final flag is :
ASCWG{f8044b06c093-f8044b06c07b}
— — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — —
Track a coin from your crypto O valley of plenty
Description:During the investigation in one of the cases, our forensics analysts were tasked with tracing the following transaction hash which occured on a trial network, and get the first address who sent money. Could you find that address?
Transaction Hash:0xa150ff06619b927cc323f16984a679a24b07265f1c1a664f1c729177929cebae
after search ifound
and start investigate

let’s show what the first address who make payout transacton to reciver

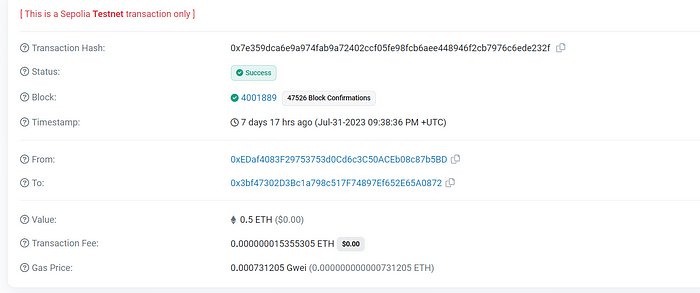
this first transaction from 0xEDaf4083F29753753d0Cd6c3C50ACEb08c87b5BD
flag : ASCWG{0xEDaf4083F29753753d0Cd6c3C50ACEb08c87b5BD}
Challenge: We have a new contract for you
Description:During further investigation on the wallet that received money that we found from the transaction hash in the previous challenge, we noticed there's a token that was generated, and used to send money as part of money laundring. Could find the last address that received tokens from this contract, and the address of the smart contract?
Flag Format:ASCWG{contract address: last wallet address}
from previous challenge i know challenge let’s show contract by show all transactions user make it ,

By clicking on contract creation i get the first part of the flag, which is the contract’s address.
0x7b799DFbbfD91ECA3E82F2378455ab09463f1C73

now we have two solutions i will use easy one
first one is easy if you know the last transction record into contract will recored on orignal transcton just look on to you will find last address recive this tokens this address 0x3a79022e90fF621cd3Cc54FE95873E1A50722B97

And now we get the second part of the flag.
Flag: ASCWG{0x7b799DFbbfD91ECA3E82F2378455ab09463f1C73:0x3a79022e90fF621cd3Cc54FE95873E1A50722B97}








